March 15, 2022
Why Does Your Business Require DDoS Protection?

What is a DDoS attack?
DDoS stands for Distributed Denial of Service attack. This involves multiple devices connected online, often referred to as a botnet. A botnet is basically deployed to distract the target website with dummy traffic.
DDoS attacks target your website and servers making them unavailable for real users. These attacks are often used as a façade for other cyber attacks taking down security systems.
Since a DDoS attack affects a huge user base, it has a significant impact, thus making it a popular means of cyber attacks for hacking groups or cyber criminals.
DDoS attacks can last for several weeks as the target struggles to recover. This has a devastating effect on the target organization, resulting in loss of revenue and brand trust.
How does DDoS attack happen?
DDoS attacks executed with networks of Internet-connected devices. These networks consist of malware infected computers, which enables them to be controlled remotely.
When the botnet is up running, the hacker can attack by sending commands to the bots. Each bot sends requests to the target’s IP address, causing the server to be congested with traffic, resulting in a DoSto normal traffic.
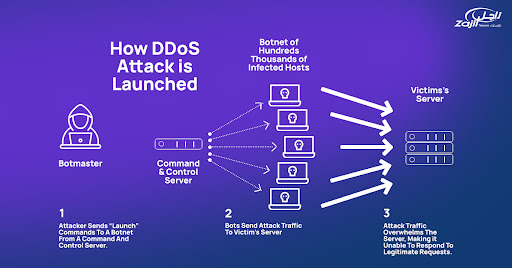
Since each bot is a physical internet-enabled device, separating the attacking traffic from the original traffic is a hassle.
- Volume Based Attacks
Includes UDP floods, ICMP floods, and other spoofed-packet floods. The intention of the attack is to douse the bandwidth of the site-under-attack.
- Protocol Attacks
This type of attack devours actual server resources, or those of transitional communication equipment, such as firewalls. Includes SYN floods, fragmented packet attacks, Ping of Death, Smurf DDoS, etc.
- Application Layer Attacks
The intention of these attacks is to crash the web server and consists of superficially genuine and acquitted requests. Includes low-and-slow attacks, GET/POST floods, attacks that target Apache, Windows or OpenBSD vulnerabilities, etc.
Protection from DDoS attack
The ease of inflicting a DDoS attack is clear from the above-mentioned points. DDoS prevention services are essential to shield digital assets of businesses. The attacks need to be prohibited by having a strategic approach:
- Defence strategy
Investigation of the network, identification of attacked nodes, and network adaptation is the technique to ensure the attacked node is cut-off first from the network without spreading and without distressing the entire network. This shall form a security policy for IT in prevention of DDoS attacks
- Staying updated
Newer techniques of continuous DDoS attacks are being strategized. Thus, staying updated about the latest types of DDoS attacks is necessary to prepare a network for proper defence.
- Experts support
In order to counter DDoS attacks, you need in-depth knowledge and understanding along with expert experience. Thus, it is always important to contact experts so that the attack is investigated properly.
How does DDoS protection work?

Organization data centers are installed on-premises with inline DDoS protection. On-premises DDoS mitigation consumes significantly less time to detect and mitigate network layer, application, and SSL-based layer DDoS attacks. However, on-premises DDoS protection is ineffective against huge volumetric DDoS attacks like cloud DDoS attacks, which renders thousands of packets per second downstream.
Zajil’s defence against high-volume DDoS attacks includes using a distributed hardware platform, the product provides industry-leading service processing capabilities and scalability. A single HiSecEngine AntiDDoS12000 delivers a 2.4 Tbit/s DDoS attack defence capability. It can respond to attacks within milliseconds, quickly blocking DDoS attacks.
Zajil’s A10 Thunder provides advanced and powerful security features to enhance network and application security and ensure predictable business operations. The Thunder Series provides unprecedented next generation DDoS protection, as well as Web Application Firewall (WAF) and many more premium features, all tightly integrated onto the ACOS foundation, and of course part of A10’s all-inclusive licensing model.
Cloud-based DDoS protection service captivates mass volumetric cloud DDoS attacks and filters out authentic and malicious traffic. This alternate solution for cloud DDoS mitigation can be further categorized into:
Always on Cloud-based DDoS Protection –
Here, the traffic of an organization is usually channelled through a local POP, thus it detects and mitigates all kinds of cloud DDoS attacks at all layers prior to reaching the organization’s services.
On-demand Cloud-based DDoS Protection –
Here, the traffic of an organization is directed to a cloud-based scrubbing centre when and only the huge volumetric traffic is detected. If a breach of a specific threshold happened, the cloud-based DDoS protection measure initiates an alteration of the incoming traffic to the cloud scrubbing centre. In this method, utilization of internet links are tracked using remote monitoring at regular intervals.
Hybrid Cloud-based DDoS Protection –
This method combines the service of on-premises DDoS protection and Cloud-based DDoS protection services and harbours the benefits of both alternatives. This is very effective as it avoids the shortcomings of both on-premises and cloud-based DDoS protection methods.
Why do businesses need DDoS protection?

Nowadays, it is not a big deal to launch a DDoS attack. Hacking as a service has moulded into sophisticated and organized businesses where dedicated tools and botnets are available for hire. Thus, amateur business firms that are employed as third-party sellers to larger businesses need DDoS protection services immediately because the threat is unforeseen.
These smaller firms are most vulnerable because they lack the resources for defense against such DDoS attacks. Such small businesses’ primary defence against cyber-attacks is called Managed Security Service Provider (MSSP). An MSSP also provides a service called DDoS Protection as a Service (DPaaS).
It is the wiser decision to subscribe to a DPassS service in order to safeguard the operation of your organization.
Zajil’s security services and products offer DDoS protection equipped with the latest technologies including Zajil’s A10 Thunder DDoS protection. Get started now!




