July 29, 2022
Cyber Security Best Practices for Businesses to Follow
We are not oblivious that the internet is the most used medium for the transfer of information. That also makes it susceptible to hackers. Besides, it raises the vulnerability of losing sensitive data or clicking on links that can install malware into your system. Cybersecurity is one of the essential criteria to safeguard your business and data.
If you want to secure your business and data, do not miss reading the 15 cyber security best practices a must follow in 2022.
Cybersecurity Best Practices to Prevent Cyber Attacks
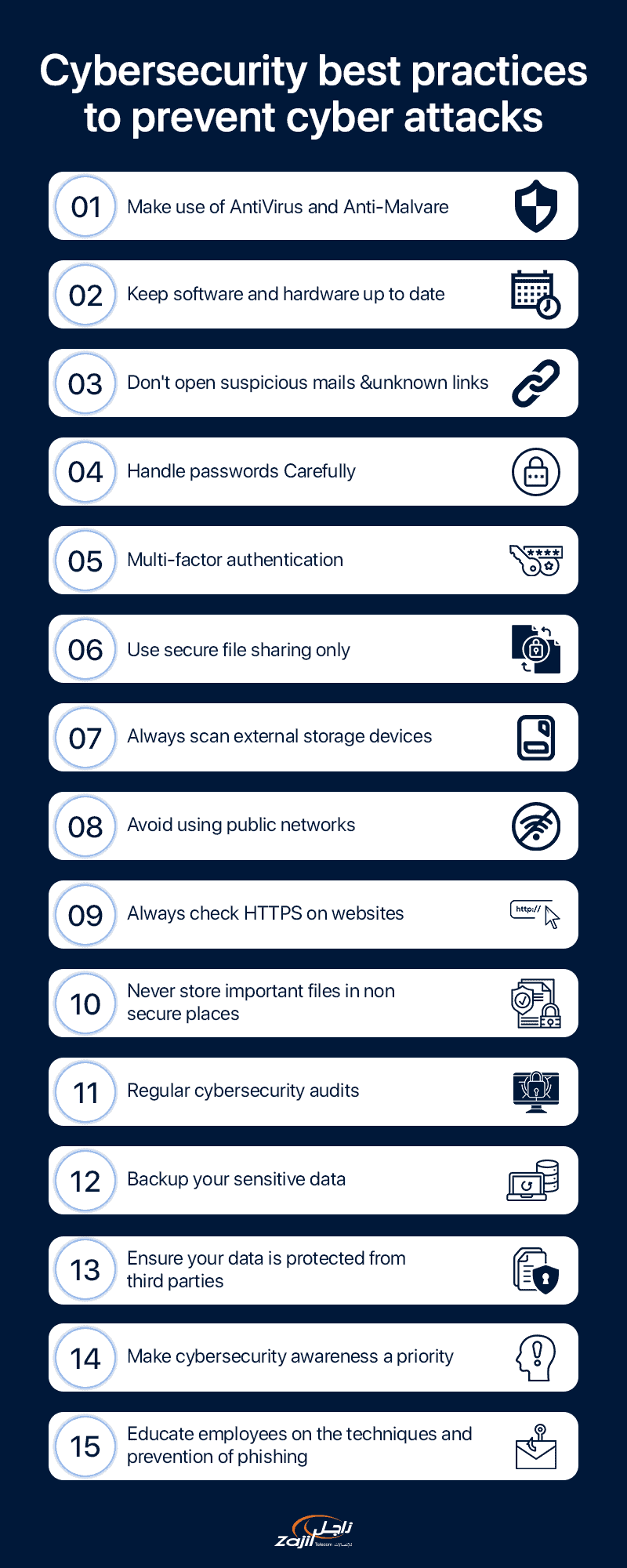
1. Make use of Antivirus and Anti-Malware
A virus attack can completely topple down your system. An antivirus acts like a wall that protects computer software from any outside attack. Anti-Malware and Antivirus detect bugs in files, applications, websites and software.
Furthermore, anti-malware and antiviruses are soldiers who protect devices from any incoming threats by scanning the system regularly. Moreover, no matter how threatening the virus is, it will be eradicated by providing automatic updates.
How does it work?
Antivirus software assesses the computer system and files against different types of malware. As hackers keep creating new viruses, the software will scan the system for any new malware threats.
The scan is conducted in three ways, viz:
- Identifying specific and known malware that are specific
- Looking for malware patterns related to a common code base that is generic
- Scanning for unknown viruses by analyzing the file structures called heuristic detection
2 . Keep software and hardware up to date
No matter how much you hate the task of updating software and hardware and the regular pop-ups, it is a must to keep your business safe and secure. An outdated software acts like a broken window making the house susceptible to bugs, threats and danger.
Do you want to know what happens if you are too lazy to update the software? That means you allow:
- Constant bug attack
- Applications and systems become unresponsive and slow down the working
- It makes your system more vulnerable to malware threats
- Outdated software fails to patch security breaches
- It can threaten your sensitive information falling into the hands of intruders
- Increases Hardware issues
- Difficulty in accessing new files or apps
How does it work?
A software update will ensure your system will outweigh any threats or dangers to your sensitive information and files.
3 . Avoid opening any suspicious emails and unknown links
They say ‘curiosity killed the cat!’ The curiosity to open emails and click on unknown links can lead you into trouble. While it is easy to click on suspicious links, it is always better to keep your curiosity in the bay.
What happens when you click on a dubious link?
Hackers are smart nuts who know to play with the mind and habits of users. These links contain malware which gets installed once clicked. And what happens next? You click the link, and bingo, your system is under the clutches of hackers.
How to safeguard your system?
- Check the sender of the email
- Ensure the source is trustworthy
- Analyze the subject line. Does it sound Phishy? Skip your idea
- What does the content speak? Check for language and grammar and does it make sense.
In short, a golden rule – Do not click on any links or attachments which are unknown or from suspicious email addresses.
Check out: FortiMail Email Security Solution
4 . Handle passwords Carefully
Your password is the lock and key that safeguards any intrusion from third parties or unknown sources. An ideal way to protect your business from hacker attacks is to preserve and secure your password.
Tips on cyber security through password:
- Keep the password long, combining numbers, characters, upper case, lower case and symbols
- Do not keep your birth date, name or anything common as your password
- Beat the hacker’s trick by writing the password in a safe place which doesn’t reach any wrong hands
- Do not save your password on any unknown system
5 . Make use of multi-factor authentication
Multi-factor Authentication (MFA) includes the user providing additional verification factors to enable access to the system. These include accessing any online account, VPN or application.
What is the purpose of MFA?
While a strong password does help in protecting your system, MFA strengthens the security. It requires users to identify more user authentication such as physical hardware or thumbprint to prevent any chance of unknown malware attacks or force threats.
How does it work?
It works by adding extra verification routes. The commonest cybersecurity best practice employed by users is encountering an OTP or one-time password every time you try to log in to the system.
6 . Use secure file sharing only
Another relevant cyber security tip is always to use secure file sharing only. Secure sharing is the process of sharing one or many files privately in a safe manner. It allows users and organizations to share files in protected mode while maintaining confidentiality.
In short, it prevents your system from intruders or any unauthorized users.
7 . Always scan external storage devices for viruses
A virus finds it way easy to infect external storage. In situations when multiple viruses infect your external drive, it can turn your entire system topsy-turvy.
For instance, a USB drive or a CD can contain viruses which can enter the system with ease. Never forget to constantly scan the external devices whenever plugged in for any virus.
How to scan for viruses?
- Install an antivirus software
- If your system does not detect viruses automatically, do it manually
8 . Avoid using public networks
Once again, the curiosity to use public networks can cost you your data. Do you know hackers know the trick of placing themselves between the connection and you through the method called Phishing?
Thus, while you think you are acquiring data from the hotspot, you share it with the hacker. Never use a public network to protect your system from falling into the hands of danger.
9 . Always check HTTPS on websites
How often do you check the HTTPS connection when visiting a website? What does the connection read? HTTPS or HTTP?
Do you know that the “s” in the HTTPS play a considerable role? The “s” stands for safety and security. An HTTPS website means the site uses a Secure Sockets Layer (SSL) certificate.
How does it work?
The connection ensures the communication is wholly encrypted, and no third party can view your activity or data.
10 . Never store essential files in non-secure places.
We know it is easier to stack all files on the computer and more convenient. The key is to lock and store data in a safe place where the hackers cannot reach it. Besides, never share your password with anyone who can easily steal the files.
Windows and Mac operating systems possess built-in tools that encrypt the files and treat the user’s password as the only way to view the files. Besides, your data and files will surely not reach the wrong hands with proper protection.
11 . Perform regular cybersecurity audits
Auditing your system for cybersecurity breaches at least twice a year will prevent you from the risk of cyberattacks. Performing regular cybersecurity audits will bring to the fore the challenges and risks related to technology and business.
How does it work?
Cyber security audits help identify security risks, malware attacks and how secure your business information is from Phishing. As per Bitdefender, periodic cyber audits prevented over 8319 threats.
12 . Make sure your sensitive data is backed up
Can backing up sensitive data help you? Yes! Keeping a backup of sensitive data will protect from losing work if the system is stolen or data hacked. It is one of the top tips for cybersecurity to back sensitive data by understanding if they pose any risk.
Back up your data on a personal or portable device with a solid encrypted passcode.
Check out: BAAS (Backup as a Service)
13 . Ensure your data is protected from third parties
Considered a top network security best practice is protecting your data from third parties. Ensure all your data, especially sensitive information, is appropriately encrypted. Avoid using third-party apps or software installed from unsafe websites as much as possible.
Download apps from PlayStore or AppStore only. The apps listed are from authorized sources, and the encrypted data protects your device against any compromise or theft of information.
14 . Make cybersecurity awareness a priority
Generating awareness of cybersecurity best practices is the most critical aspect. Lack of adequate knowledge can pose a threat to your sensitive data and also enhance the risks.
Cybersecurity is not only the organization’s responsibility, but the onus also lies on employees to take ownership of protecting businesses against any unforeseen hacker or virus/ malware attacks.
15 . Educate employees on the techniques and prevention of Phishing
Educating employees about phishing and malware attacks is imperative to keep the business away from any fraud. Typical phishing attacks include email frauds, clicking on dubious links, using public hotspots or networks, etc.
How to negate the risk?
Train your employees about the different phishing attacks and how to deal with them. Besides, understanding the core point to look for to identify a phishing attack will save your business from losing your personal information.
Conclusion
With most information and transactions performed online, the importance of cybersecurity is at an all-time high. Avoid unnecessary hacks, Phishing or password theft by educating oneself on the top network security best practices to follow. If you need any further cyber security advice or if you need any cyber security services, please don’t hesitate to contact us. We provide all types of cyber security services at Zajil.




